MCQ Test 3 Reflection
Reflection on MCQ Test
 |
Home | About Me | Time Box | Funny picture of a bird | Java Testing | Java Table | API |
|---|
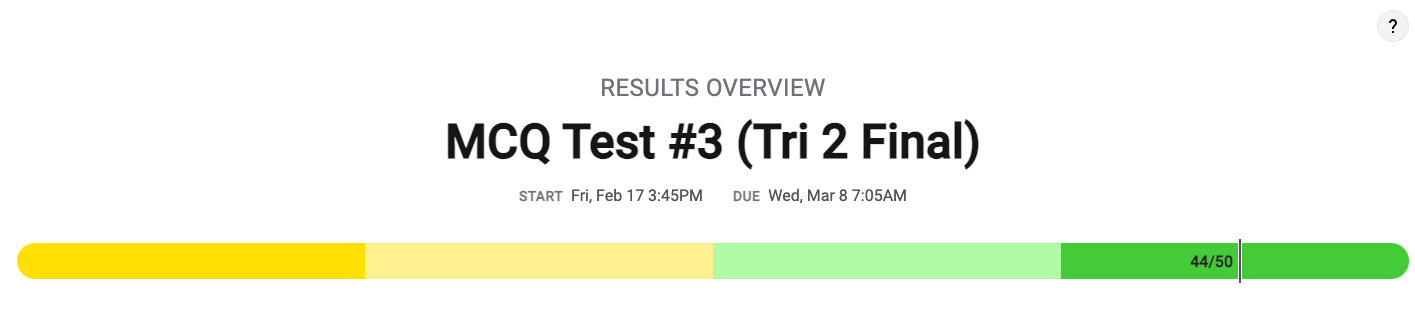
Score: 44/50
Corrections
Q2: Compromising a user’s personal privacy
Which of the following has the greatest potential for compromising a user’s personal privacy?
- Original answer:
- The Internet Protocol (IP) address of the user’s computer
- Correct answer:
- A group of cookies stored by the user’s Web browser
- Explanation
- Cookies may include tons of data about the user, including usernames and passwords to accounts, whereas the IP Address does not have information relating to the user.
Q28: Remove first and last two characters of string
Consider the following procedures for string manipulation.
Procedure Call
Explanation
concat(str1, str2)Returns a single string consisting of str1 followed by str2. For example, concat("key", "board") returns "keyboard".
substring(str, start, length)Returns a substring of consecutive characters from str, starting with the character at position start and containing length characters. The first character of str is located at position 1. For example, substring("delivery", 3, 4) returns "live".
len(str)Returns the number of characters in str. For example, len("pizza") returns 5.
concat(str1, str2)str1 followed by str2. For example, concat("key", "board") returns "keyboard".substring(str, start, length)str, starting with the character at position start and containing length characters. The first character of str is located at position 1. For example, substring("delivery", 3, 4) returns "live".len(str)str. For example, len("pizza") returns 5.- Original answer:
newString ← substring(oldString, 3, len(oldString) - 2)-
tempString ← substring(oldString, 3, len(oldString) - 2)
newString ← substring(tempString, 1, len(tempString) - 2) - Correct answer:
newString ← substring(oldString, 3, len(oldString) - 4)tempString ← substring(oldString, 3, len(oldString) - 2)
newString ← substring(tempString, 1, len(tempString) - 2)- Explanation
- The original answer is incorrect because it will only remove the first two characters of the string. The correct answer is right because the substring with second parameter of 3 makes it so the first 2 letters are removed, then the third parameter removes the last 2 by ending at the length of the string minus 4, because 4 characters are removed in total.
Q40: Move robot back to starting place
The following grid contains a robot represented as a triangle, which is initially in the bottom-left square of the grid and facing the top of the grid. The robot can move into a white or a gray square but cannot move into a black region.

The following code segment implements an algorithm that moves the robot from its initial position to the gray square and facing the top of the grid.

When the robot reaches the gray square, it turns around and faces the bottom of the grid. Which of the following changes, if any, should be made to the code segment to move the robot back to its original position in the bottom-left square of the grid and facing toward the bottom of the grid?
- Original answer:
- Interchange the ROTATE_RIGHT and the ROTATE_LEFT blocks.
- Correct answer:
- No change is needed; the algorithm is correct as is.
- Explanation
- With the original answer, the robot would leave the boundaries. I honestly don't even know why I picked that because the correct answer is so obviously correct.
Q41: Using binary search on list of genetic codes
A large number of genetic codes are stored as binary values in a list. Which one of the following conditions must be true in order for a researcher to obtain the correct result when using a binary search algorithm to determine if a given genetic code is in the list?
- Original answer:
- The genetic codes must be converted from binary to decimal numbers.
- Correct answer:
- The list must be sorted based on the genetic code values.
- Explanation
- Numerical base does not matter in binary search, as long as they are sorted.
Q49: Crowd Flow Simulation
A city planner is using simulation software to study crowd flow out of a large arena after an event has ended. The arena is located in an urban city. Which of the following best describes a limitation of using a simulation for this purpose?
- Original answer:
- The model used by the simulation software cannot be modified once the simulation has been used.
- Correct answer:
- The model used by the simulation software often omits details so that it is easier to implement.
- Explanation
- Modification is one of the benefits of simulations so I have no idea why I picked this. However, simulations lack complete accuracy because they do not account for every possible factor and thus they are not completely detailed.
Q50: Which algorithm runs in a reasonable time
A computer scientist is analyzing four different algorithms used to sort a list. The table below shows the number of steps each algorithm took to sort lists of different sizes.
List Size
Number of Steps
for Algorithm A
Number of Steps
for Algorithm B
Number of Steps
for Algorithm C
Number of Steps
for Algorithm D
1
10
2
1
1
2
20
4
2
4
3
30
8
6
9
4
40
16
24
16
5
50
32
120
25
Based on the values in the table, which of the algorithms appear to run in reasonable time?
Select two answers.
for Algorithm A
for Algorithm B
for Algorithm C
for Algorithm D
- Original answer:
- Algorithm B
- Algorithm C
- Correct answer:
- Algorithm A
- Algorithm D
- Explanation
- Misunderstood the question. A and D increase in steps the slowest and thus require less steps than the other two algorithms